Digital Certificate
- Shuvam Aich
- May 20, 2021
- 8 min read
Updated: Aug 24, 2021
Digital certificates are electronic credentials that bind the identity of the certificate owner to a pair of electronic encryption keys, (one public and one private), that can be used to encrypt and sign information digitally. The main purpose of the digital certificate is to ensure that the public key contained in the certificate belongs to the entity to which the certificate was issued, in other words, to verify that a person sending a message is who he or she claims to be, and to then provide the message receiver with the means to encode a reply back to the sender.
Encryption techniques using public and private keys require a public-key infrastructure (PKI) to support the distribution and identification of public keys. Messages can be encrypted with either the public or the private key and then decrypted with the other key. Without certificates, one could send data encrypted with the private key and the public key would be used to decrypt the data, but there would be no assurance that the data was originated by anyone in particular. All the receiver would know is that a valid key pair was used. In essence, a Certificate Authority or CA then is a commonly trusted third party that is relied upon to verify the matching of public keys to identity, e-mail name, or other such information.
The Certificate Authority (CA) packages together in the one certificate the public keys, information about the encryption algorithms used, the owner or subject data, the digital signature of a Certificate Authority that has verified the subject data itself, and a date range during which the certificate can be considered valid. Digital Certificates can be used for a variety of electronic transactions including e-mail, electronic commerce, groupware and electronic funds transfers.
Example
Consider a user who wants to shop online through an online shopping web site such as Amazon. The user types the link to the Amazon web site and the web browser connects to the web site. The main concern here is whether the web site truly belongs to Amazon company or is it a malicious party posing to be Amazon. To solve this trust issue, digital certificates are used in a public key infrastructure, and a trusted third party is used which can establish the identity of the entity and integrity of the public key.
Certificate Structure
The X.509 certificate standard is widely used to structure digital certificates. There have been three versions of this standard and at present version 3 of this standard is being used.
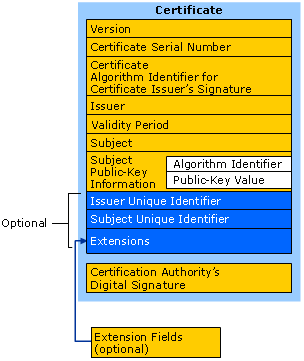
There are ten basic fields in a digital certificate. Six of which are mandatory and four are optional fields. The mandatory fields are:
• Serial number
• Signature algorithm
• Issuer name
• Validity period
• Subject name
• Public key information
The optional fields are:
• Version
• Issuer unique ID
• Subject unique ID
• Extensions
These optional fields are used in version 2 and version 3.
Version: This field specifies the version number of the certificate. This can be either version 1 or 2 or 3. When extensions are included10 3 Public Key Infrastructure (PKI) in a certificate, this field indicates version 3. If the it includes unique identifiers without extensions, then it is version 2. If it does not include extensions and unique identifiers, then it is version 1.
Serial number: It is a unique positive number assigned for each certificate. It is assigned by the issuer to identify the certificate. Signature Algorithm: This field indicates the algorithm used by the issuer to sign the certificate. Some examples are: RSA encryption algorithm with SHA-1 hashing algorithm, RSA with MD5 or DSA with SHA-1 algorithm.
Issuer: This field indicates the X.500 Distinguished Name of the trusted third party which signed and issued the certificate.
Validity: Validity indicates the date from when the certificate is valid (i.e. valid from) and the date until when the certificate is valid (i.e. valid to).
Subject: Subject is the distinguished name of the entity that owns the certificate. The owner is the entity associated with the public key in the certificate. Owner can be a CA, RA, person, company, or application.
Public key information: This field contains the public key of the subject and the algorithm identifier.
Issuer unique ID: This is a unique identifier to facilitate the reuse of issuer’s name over time.
Subject unique ID: This field contains a unique identifier to facilitate the reuse of subject’s name over time.
Extensions: This field is present in version 3 certificates. The extensions are used to give more information about the certificate which is not given by the basic fields. Extensions have three basic elements: an extension identifier, criticality flag and extension value. Extension identifier gives the format of the extension value, criticality flag indicates that the extension is important. Some of the extensions are: key usage, subject name alternative, basic constraints, policy constraints, name constraints etc.
Public key infrastructure provides an effective authentication method through digital certificates. It ensures a secure communication that is necessary in today’s world as majority of the transactions are online. It provides secure exchange of confidential information. Certificates are being used in various network applications and enterprises. Usage of certificates is not limited to personal computers, they are widely being used in smart phones, smart card and other devices as well
Digital Certificate Creation
The steps required to create a digital certificate involves three parties first the end user, second the registration authority and third is certificate authority. The end user request for a digital certificate and the request goes to the registration authority(RA) which then assist the certificate authority(CA) to create the digital certificate. Registration authority act as a intermediate between end user and the certificate authority. It also assist in day to day task of certificate authority.

Services of Registration Authority:
Accepting and verifying the details of new user’s registration.
User key generation.
Backups and recovery of key.
Certificate cancellation.
Steps for Digital Certificate Creation:
Step-1: Key generation is done by either user or registration authority. The public key which is generated is sent to the registration authority and private key is kept secret by user.
Step-2: In the next step the registration authority registers the user.
Step-3: Next step is verification which is done by registration authority in which the user’s credentials are being verified by registration authority. It also checks that the user who send the public key have corresponding private key or not.
Step-4: In this step the details and sent to certificate authority by registration authority who creates the digital certificate and give it to users and also keeps a copy to itself.
How does a CA verify a Certificate?
There are some issues that the certification authority need to take care of while issuing a digital certificate. To begin with, a certificate authority need to sign a digital certificate. CA always signs a digital certificate with its private key. CA says, “I have signed this certificate to guarantee that this user possesses the specified public key.” This is required because there has to be some means for finding out whether the document that is being claimed as a
digital certificate has actually being claimed by the concerned authority or not. So in order to do that, the digital certificate will be signed by the certification authority with a digital signature.
Message digest of the entire digital certificate is created.
This message digest is now encrypted using the private key of the certification authority.
After being encrypted, what we get is the digital signature. So the digital certificate will also contain the digital signature of the certification authority.
Now when this digital certificate is being received by someone, that someone can verify the authenticity of the digital certificate by finding out whether the CA has actually issued it or not by verifying this digital signature.
How to verify a digital certificate?
We would again make use of the message digest algorithm and create the message digest (MD1)
After creating the message digest, the digital signature would be decrypted using the decryption logic and another message digest is generated(MD2). This decryption is only possible if the person verifying knows the public key of the certification authority. If the person does not know the public key of CA, then a query has to be sent for obtaining it.
Once it has been generated, the two message digests can be compared to find out whether the certificate is acceptable or not.

Working of Digital Certificates
Digital Certificates in a Public Key Infrastructure work in the following way:
1. Consider an online shopping web site such as Amazon. The server of the Amazon company requests for a digital certificate from a certificate authority.
2. The certificate authority verifies the identity of the company and generates a digital certificate. It hashes the contents of the certificate and signs (encrypts) the hash value using its private key. It includes this signature in the certificate and issues the certificate to the company.
3. A user who wants to connect to the Amazon web site enters the HTTPS web address in his browser. The browser tries to connect to the web site.
4. A digital certificate is sent from the web server of the Amazon company to the browser.
5. When the browser receives a certificate from the web server it performs the following tasks:
• It checks whether the CA who signed the certificate is trusted by the browser. The browser already has the trusted CA12 3 Public Key Infrastructure (PKI) certificates installed, so it has the public key information of the CA.
• With the public key of the CA, the browser decrypts the signature in the company’s certificate and obtains a hash.
• It also computes a new hash of the content in the certificate.
• If both the hashes match, then the signature in the certificate is verified to be signed by the trusted CA and the public key in the certificate is valid.
• Now the name in the certificate is checked against the web site’s name. If it matches then a secure connection is established for the online transactions.
• The browser also checks whether the certificate is within its expiry period.
All this process is transparent to the user and it is carried out in milliseconds. The integrity of the certificate is guaranteed, as long as the CA’s signature can be verified. It also makes sure that the public key in the certificate is valid and has not been tampered with. It13 3 Public Key Infrastructure (PKI) guarantees that the public key belongs to the owner of the certificate
and it can be used for secure communication. Checking the name on the certificate against the web site’s name helps in preventing man-in-the-middle attacks, where a malicious user modifies the certificate and claims to be the site that the user wants to establish communication with.
How to know that a web site has valid certificate?
A site which is secured with a digital certificate has a ’https://’ as a prefix to the web address. This means ”secure HTTP”. When a browser connects to a https site, it displays a padlock symbol or a green browser bar (depending on the browser being used), to show that the web site has a valid certificate and is trusted.
Advantages and Disadvantages
Advantages of using Digital Certificates in Public key Infrastructure:
1. Authentication: By using digital certificates the identity of the entity can be verified.
2. Secure: It assures that the public key belongs to the owner of the certificate an so a secure communication can established for confidential email, e-commerce and online transactions.
3. Integrity: Integrity is guaranteed a long as the CA’s signature on the digital certificate can be verified.
4. It prevents man-in-the-middle attacks, where a malicious user pretends to be the web site that the user wants to connect with.
5. Non-Repudiation: The signature on the certificate guarantees that only the web site owner has the private key associated with the public key in the certificate.
6. The process of verification and authentication is transparent to the end user and the process of authentication takes only a few milliseconds.
7. Certificates are supported by many enterprise networks and applications.
Disadvantages are:
1. A browser does not give a warning when a web site changes the certificate.
2. A user has to blindly trust that the developer of the OS has installed genuine root certificates and not fraudulent certificates.
3. A fraudulent root certificate can be installed in the browser when a malicious user gains access to the personal computer. In this case the browser will not report any security warning while browsing sites that use the fraudulent certificate





Comments